Resilient DNS security
Stop DNS threats before they take your services offline
Path's DNS protection safeguards your domains by blocking spoofing, amplification, and DNS-based attacks before they impact your network.
<10 miliseconds
Average resolution time across all global queries
3B+
DNS requests processed with built-in threat detection
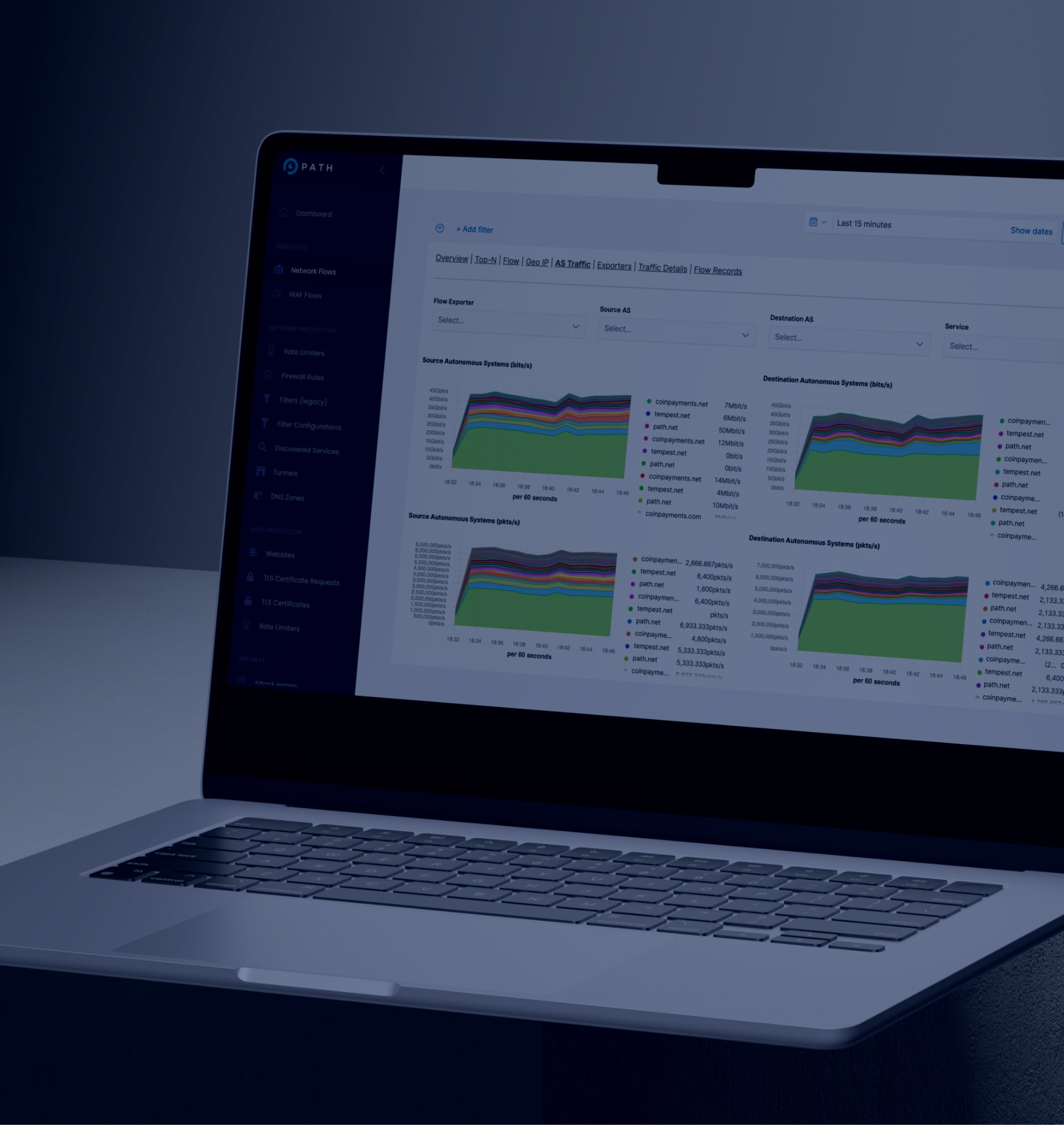
Real-world impact
Who benefits from Path’s DDoS protection
From fintech to national security, Path protects the systems that can’t afford to go offline.
Hardened security
E-commerce businesses
Keep transactions safe and uninterrupted, with a DNS solution that defends against spoofing and redirection.
Fast, reliable access
SaaS providers
Deliver a seamless experience to users with secure DNS routing and high-performance availability.
Regulatory compliance & resilience
Fintech and healthcare
Maintain secure, compliant infrastructure with DNS protection designed for sensitive industries.
Threat coverage
What Protected DNS defends against
DNS amplification
Attackers exploit open DNS resolvers to send overwhelming volumes of traffic to your servers. By amplifying small requests into large responses, they generate massive floods without needing high bandwidth themselves.
DNS tunneling
Used to sneak data past firewalls, DNS tunneling disguises malicious traffic as regular DNS queries. Path detects and blocks these covert channels before sensitive data can be extracted or threats can move laterally.
Cache poisoning
Malicious actors attempt to inject false DNS records into caches, rerouting users to fake or harmful websites. Path ensures the authenticity of DNS responses, preventing these redirects and maintaining trust in your domain.
Spoofing attacks
Blocks forged DNS responses designed to mislead users or redirect them to malicious websites. Path verifies response integrity to ensure users always reach the correct and trusted destination.
Domain hijacking
Prevents unauthorized changes to your DNS records that could reroute traffic or compromise your domain. Path ensures domain ownership stays protected and fully in your control.
Intelligent routing
Smarter traffic routing for faster, resilient DNS
Global Anycast DNS routes queries through the nearest reliable server for fast resolution, even during attacks. On-prem options support strict compliance.
Globally distributed Anycast infrastructure
Instant failover for built-in redundancy
Consistent low-latency performance worldwide
Threat detection
Real-time filtering stops threats at detection
Path inspects each request at the edge, blocking spoofed or malformed DNS traffic without slowing legitimate queries.
Tuned to your app’s traffic patterns
Learns from previous threats
Enterprise-grade reliability
Secure architecture
Zero-trust design built to safeguard your domain
With hardened systems and no reliance on third-party DNS providers, Path keeps your domain name system secure, reliable, and in your full control.
No third-party exposure
End-to-end encryption support
Configurable access control
What you gain
Key benefits of Path’s Protected DNS
From uptime to user trust, DNS is the backbone of your digital presence. Path’s protection keeps it reliable, secure and fast at all times.
Stay online, even during attacks
Built-in failover and global distribution ensure your domain stays reachable in every region, even under heavy load.
Fast, consistent DNS resolution
Edge-level routing shortens query paths, reducing DNS lookup times and speeding up your entire platform.
No third-party reliance
Path runs its own DNS infrastructure, giving you full visibility and eliminating exposure from external DNS providers.
Defense from common DNS threats
Spoofing, tunneling, poisoning are all filtered by Path’s protective layer to keep your platform safe from downtime or data leaks.
Real-world results
Proven performance across high-traffic platforms
Path’s DNS protection keeps your domains online and responsive, even under pressure. Here’s how it holds up when it counts.
15 milliseconds avg. resolution
Fast global response
30M+ queries/day
Filters threats at scale
60+ edge locations
Resilient infrastructure
70% reduction in spoof attempts
Proactive threat blocking
Full-stack security
Extend protection across your full stack
Go beyond traffic filtering with full-stack safeguards for apps, domains, and infrastructure.